The WannaCry cyber attack that targeted Microsoft Windows operating system in 2017 infecting over 200,000 computers in over 150 countries, drew greater attention to ransomware and software security in general. So what is ransomware and what should you know about it? Read on!
About Ransomware
Ransomware is a type of malware that denies a victim access to data on their device until a ransom is paid. This malicious software could also issue a threat, such as to delete or destroy the data, in the event of the victim failing to make necessary payment.
You could simply think of a ransomware attack as kidnapping – in this case, that of data. You are made to pay to secure the release of your ‘kidnapped’ data. The ransom payments typically have a time limit and are received via anonymous payment systems such as Bitcoin.
While many people may be learning about ransomware attacks for the first time, they are not new. The first of this malware is said to have surfaced back in 1989. The crudely-implemented malicious code by Joseph Popp was known as the AIDS Trojan or PC Cyborg. Victims were required to send a $189 ransom to a post office box located in Panama!
The use of more advanced techniques and Bitcoin for payment has led to a surge in the number of extortion ransomware in recent years. The malicious software became especially more prominent from around 2005.
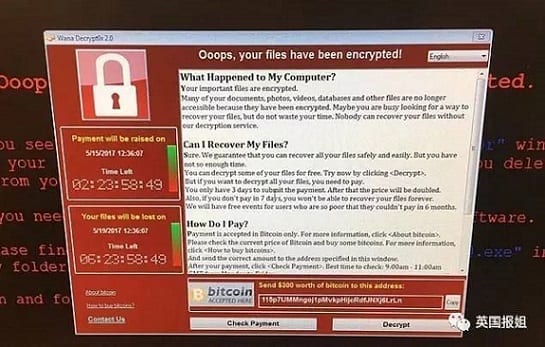
Wannacry is the latest Ransomware in town. It has so far infected over 200,000 Windows computers in over 150 countries requiring victims to pay $300 in Bitcoin to gain access to their computers.
Types of Ransomware
There are different types of this cyber threat. The most common ones are:
Encryption ransomware – This uses advanced encryption schemes to block personal files and folders. You are promised a special decryption key after paying an amount. CryptoLocker is a notable example.
Lock screen ransomware – This is a piece of non-encrypting ransom-based malware. Lockers lock the screen of your device, making it impossible to access files. Some rely on threats (such as copyright infringement or pornography) to get ransom money. An example is WinLocker.
Master Boot Record (MBR) ransomware – This is also a variation of lockers. The threat alters your computer’s MBR, preventing boot up from completing successfully. You get a message on the screen telling you to pay an amount to restore access.
Of these, encryption ransomware is the most widespread and the toughest to deal with. The malicious software, also known as crypto-ransomware, can encrypt all file types and scramble file names. It will be practically impossible to get these files back without paying for a decryption key.
There is also mobile ransomware, which mainly targets Android OS.
Notable Ransomware Families
A scary thing about ransomware is that many of the different types come in variants. That is newer versions are released from time to time to keep the threat on. These different versions make up families. The most notorious ones include:
- CryptoLocker
- Reveton
- Locky
- TorrentLocker
- CryptoWall
- Fusob
- Cerber
- Uiwix
- WannaCry
It is WannaCry that again drew significant attention to these cyber threats. The large-scale attack, described as the biggest in the history of the Internet, started 12 May, 2017, affecting many major organisations in Europe. Those affected included Telefonica, the British National Health Service (NHS), Renault, FedEx and Russia’s MegaFon were some of notable names affected.
WannaCry exploited vulnerability in Windows, for which Microsoft had reportedly released a critical patch two months earlier. Each victim was allegedly asked to pay $300 via Bitcoin cryptocurrency. But a source revealed affected businesses paid as much as $40,000 in ransom. The ransomware attack is now said to have spread to some 150 countries.
Who Are the Targets?
You will be disappointed to learn cyber criminals behind these attacks, by and large, are indiscriminate in their choice of targets. An ordinary consumer, a business, or even a government institution will do. For instance, they can target home users because of their perceived laxity about cyber threats and typical failure to have data backups.
Businesses and large institutions are, of course, the more enticing targets, even though they tend to be more security conscious. A successful attack of any member of the latter group will definitely fetch more money. Cyber criminals target public institutions mainly for the wealth of personal and confidential information at their disposal. Basically, you are a potential target of a ransomware attack, if you are not a victim already.
How Do Infections Spread?
There are various means through which ransomware attacks can be perpetuated. Usually, the focus of the criminals is to look for a vulnerability to exploit. The following are some of the popular methods:
- Spam emails containing malicious links or attachments that release malware into user’s system when activated
- Injection of malicious codes into legitimate websites, with these being released into a user’s system when they visit.
- Affiliate schemes involving ransomware-as-a-service, in which the malware creator gets a cut every time a ransom is paid
- Exploitation of security vulnerabilities in out-of-date software
- Redirection of Internet traffic to malicious online platforms
- Botnets
- Drive-by-downloads
- Malvertising campaigns
The presence of ransomware may not be immediately obvious following infection. It operates discreetly in the background until the locking mechanism is activated.
What Can You Do to Immune Yourself Ransomware Infection?
Your best bet is to keep ransomware attack at bay by all means. Here are some tips you may find helpful:
- Ensure your operating system, browsers and applications are up-to-date at all times
- De-activate the macros function in Microsoft Office as that is targeted in ransomware attack
- Install an ad-blocker
- Avoid opening spam emails (most importantly, do not click any links in such)
- Do not download attachments in emails from unknown senders
- Do not store your important data on only your PC or mobile device – have multiple backups on external drives or in the cloud
- If you are using a cloud storage service such as Google Drive for backup, do not leave it on by default
- Remove redundant browser plug-ins and set to ask me for activation of those you’d love to keep
Antivirus programs cannot be relied on entirely to protect you against ransomware, at least not for now. You need to be proactive in protecting your data from cyber criminals. These villains have all the incentives to continue with their attacks, which is why you need to be vigilant.