Latest Internet Security Posts
AI and How Cyber Criminals Are Using It To Hack Servers
2023 is probably going to be remembered as the year of artificial intelligence.
Across 2023, artificial intelligence was adopted by security firms, marketing teams, and a wide array of other businesses around the globe.
It seems that in 2024, AI is set to be an unstoppable force and surely it can only be used for good, can’t it? Unfortunately, that is wrong. Artificial intelligence has the advantage of being quick and precise, making it the ideal tool for cybercriminals to hack secure and sensitive information.
So, how is AI being used to target businesses, and how can you protect yours from an...
Opera Mini launches Locked Mode for PIN-Protected Browsing
Global browser innovator Opera today announced a significant privacy enhancement to Opera Mini with the introduction of Locked Mode, which enables PIN-protected browsing to further boost privacy protections. The move addresses the needs of 94%* of mobile users who have requested increased password protection features, particularly when sharing devices with family or friends.
The new Locked Mode allows users to set a PIN that is independent from the device’s main lock code, which secures their tabs, history, and stored data, thus granting them greater control over their mobile browsing.
Users can now share their phone with family and friends, comfortable in...
Online Safety for Children – An Introduction
Keeping your kid safe is the primary concern of any parent. However, the emergence of the Internet, creates a potentially harmful environment making this job a lot harder. What is more, due to the wide-spread accessibility of connectivity, as well as the multiple devices it can be accessed on, there is all the more content taking up huge chunks of your child’s time daily.
Considering the parts of the day children stay hooked to their Internet-connected device, smartphone, tablet or laptop, it has been pivotal to try and understand what they spend the most time on.
In this regard, research stats...
VIPRE Antivirus Plus – Search and Share Safer
VIPRE has rolled out the Antivirus Plus edition of the VIPRE Antivirus. VIPRE Antivirus Plus comes with features to keep you safe while you search online and share with your friends on social media websites. It protects you against identity thieves, spammers, hackers and cyber-criminals, keeping your PC safe without impacting performance.
VIPRE Antivirus Plus comes with Web Protection that identifies and alerts you of links that could be infected with viruses and other malware. The antivirus also offers protection from malware, spyware, and ransomware. It will detect and remove all types of malware, spyware, and ransomware from your computer.
VIPRE...
4 Steps to Protect Children’s Safety and Privacy Online
Parents know how hard it can be to keep their children safe from online dangers. As time goes by, these dangers multiply and take different forms which are more and more complicated to keep an eye on. Complicated, yes, but it's not an insurmountable task.
Every manufacturer of security suites on the market is hard at work to keep your kids safe from malicious people and their ways to steal sensitive information. Avast is only one of them and they're mighty good at what they do.
Children have always been one of the favorite targets of hackers everywhere. As they continue...
Ivacy VPN — Features and Pricing Plans
Need a VPN with industry standard encryption and security features that allows you stream contents on the Apple TV or Amazon's Fire TV stick, or to bypass several regional restrictions? Then you should check out Ivacy VPN. But before you jump right ahead to the features of the VPN, you might want to read a little bit of history of company behind this player in the VPN marketplace.
To checkout the pricing of Ivacy VPN, Click Here.
Ivacy VPN: Company Profile and History
Ivacy entered the VPN ecosystem as far back as 2006 and has ever since skyrocketed to being one of...
What is IP Spoofing and How can you Protect yourself?
IP spoofing occurs when hackers impersonate another user or device on a network so that they can spread malware, bypass access controls, and also steal data. Spammers and hackers use this technique to access financial and personal information. IP spoofing involves hackers creating an IP that has a fake source address as the headers.
This IP often has fake information, which hides the identity of the hacker, and can help him/her launch a cyber-attack. IP spoofing allows cyber-criminals to undertake fraudulent activities such as scamming or spamming undetected.
Even if an attack gets discovered, it is quite difficult to trace its...
6 Simple Ways to Hide Your Activities Online
Every time you go online, you’re tracked by ISPs, governments, advertisers, and other third-parties who want to get their hands on your personal info. With no real default privacy on the Internet, it only makes sense to cover your tracks from the prying eyes that may be watching.
However, while there are many different ways you can go about this, the question remains: which ones are actually worth your time?
In this post, we take a look at 6 ways take to hide your identity online. So, let’s get started:
1. Surf the Web Anonymously with a VPN
Anonymous surfing is made easy...
Protecting Consumer Data When It’s All Over the Internet
Big data has been a boon to businesses large and small. Over the last decade, companies have begun collecting and using consumer data to improve their marketing strategy, products, and customer experience. While this use of big data has led to a competitive edge, it also has a downside: risks to consumer privacy and sensitive company information.
Cybercrime is on the rise, and data is our most valuable asset. Losses from cybercrime are expected to reach a staggering $6 trillion by 2021, and many of these attacks target small businesses.
Consumers need to be wary of any attempt to steal their...
5 Best Server Security Tools for Overall Cyber Protection
Server security tools focus on protecting physical servers, from safeguarding admin privileges to login credentials. In addition, antivirus software can be configured on each server to protect them from any malicious activity, and endpoint monitoring is critical.
Still, it often feels today like physical servers have become just another end-point for malicious attackers to exploit. And with the rapid advancement of technology, bad actors have more resources than ever, and cybersecurity experts must constantly battle this threat.
To this end, we'll take a look at why server security is so vital for organizations and a few ways you can make your...
What to Do if You Receive a Mail Saying Your Information...
There are many ways your information can be compromised. Businesses try hard to account for security vulnerabilities by using a zero trust security model, implementing endpoint detection and response, and choosing the vendors they work with wisely, but smart hackers can still gain access to their systems.
If you shop or do business with one of these companies or organizations, your information can be compromised, even though you didn’t do anything wrong.
Fortunately, businesses and organizations are required to tell you if your information has been compromised, but exactly what should you do when you get a mail that your information...
3 Types of SSL Certificates offered by Web4Africa
SSL Certificates are no longer an optional choice but a necessity, especially for e-commerce websites or other forms of transactional websites and web apps. Encrypting the web traffic between a web browser and a web server has become absolutely necessary.
SSL Certificates are available from Web4Africa at affordable prices. Also, the certificates are issued within a few minutes in most cases, provided the client follows the required steps to enrol and authenticate the domain name or hostname being secured.
Web4Africa is a leading web hosting company that offers world-class services related to websites including domain name registration, web hosting, virtual servers,...
Suffered a Company Data Breach? 7 Initial Steps to Take
Most small business owners are under the mistaken impression that data breaches and cyber attacks are directed only at large corporate giants such as Google, Target, Citibank, and Anthem to name a few.
However, Small Business Trendz reports that 43% of cybercrime targets small businesses. Further, 60% of businesses are likely to close down within 6 months of becoming victims of hacking incidents.
Given these statistics, a wise option is to take all the necessary steps to protect your company from the possibility of such information leaks. If, despite your best efforts, you find that a data breach has occurred, you...
Cybersecurity: Can we really be Safe?
Cybersecurity: can we really be safe?: Based on our observation, the answer is no. This is because if a hacker or insider threat wants to get into your network and steal your information they will.
The best companies can do is make it as difficult as possible for them to achieve their goal. By setting up alerts and parameters business can start to be more proactive rather than reactive to the outcome of a data breach.
I would be happy to go into more detail, but without any guidance from your side, I am unsure of what specifics to drill down...
ZoneAlarm PRO Antivirus and Firewall
Secure your PC and your web browsing activities with ZoneAlarm Antivirus and Firewall. ZoneAlarm Antivirus detects and blocks spyware, viruses, worms, Trojan horses and rootkits, while the Firewall monitors programs for suspicious behaviour locking out hackers and blocking intrusions, keeping you and your computer safe from malicious attacks.
Download ZoneAlarm PRO Antivirus + Firewall 2013 - Save 50%+ today!
ZoneAlarm is well known for their superior firewall which shields your computer from hackers, virtually making your PC invisible online. The antivirus monitors your PC for activities of viruses, spyware and Trojan horses and blocks them.
ZoneAlarm comes with a Private Browsing feature...
Best Black Friday VPN Deals 2023
Black Friday is the most awaited time of the year for bargain hunters and discount lovers. After all, it brings amazing discounts and deals on a variety of products and services, VPN being one of them. In this article, we look at some of the best Black Friday VPN deals you can get right now.
If you’re looking to buy a VPN for privacy and anonymity online without denting your wallet, this is the best time to get one for a fraction of the cost as almost every popular is offering exclusive deals for Black Friday.
We have rounded up some...
Why You Need A VPN This Black Friday?
You may have already come across numerous articles recommending the best VPNs for all your internet needs and requirements.
What these articles fail to do is to give you an in-depth explanation as to how VPNs can actually help you, and in what cases in particular.
Seeing how Black Friday is around the corner, you may know it is necessary to use a VPN, but how will it actually help you at all? If you want to learn more about it, read on.
You may also be interested Best Black Friday VPN Deals.
What is a VPN?
VPNs are tools that allow you to...
How to Keep Your Personal Information Secure Online?
The Internet we all love and depend on isn’t a safe place these days. Viruses, malware, and phishing scams are increasing in quantity and sophistication worldwide. Incidents of data breaches and identity theft are on the rise.
“Reputable” sites track your every move and store your personal information without you even knowing about it.
While protecting your online privacy has become harder, it’s now more important than ever. Follow these 7 simple ways to keep your valuable data private on the web.
1. Anonymize Your Connection
By going anonymous online, you can protect yourself from anybody trying to spy on your browsing sessions...
6 Timeless Tips for Data Privacy and Security on Your Windows...
There are many estimates that suggest that the number of Windows PC users in the world is in the over a 1 billion range. This makes Windows PCs very attractive to hackers and makes cybersecurity and data privacy a top priority of any Windows PC owner.
From banking details to private conversations, your PC is a treasure trove of personal information that could lead to devastating consequences if left unprotected. Wondering how to fortify your virtual fort?
You've come to the right place. We will be highlighting six tips that will enhance your data privacy and reinforce your cybersecurity measures, shielding...
All About Virtual Private Networks
A VPN is one of the most important tools that is used for securing your personal data and protecting your privacy online.
What is a VPN?
A VPN, or virtual private network, is an on-demand private tunnel through the internet. It provides a secure and private network connection through the public internet.
Top VPN services let you bypass censorship, content blocks, and website restrictions and hide your IP address when you use the internet and protect your personal data.
VPNs hide your IP address and physical location while encrypting your internet traffic to keep you anonymous so that no one can tell who...
AI and Machine Learning in Cybersecurity Threat Detection
Cybersecurity and online threats are ubiquitous these days. It seems like every other day, we're hearing about some data breach, a person being doxxed, or someone, somewhere, falling victim to a cybersecurity threat.
Traditional security measures aren't up to the task anymore, and an antivirus/firewall combination simply won't cut it anymore. Today's tech-savvy individuals need a more comprehensive solution to protect themselves online.
It doesn’t matter if you run a small business, work from home, or simply want to keep your family safe online. AI and machine learning can help. Here’s how:
The Evolution of Cyber Threats
Take a moment to check the...
Vanguard Website may Harm your Computer according to Google
This article was written on 10th July, 2012 when the website of Vanguard was momentarily flagged by Google for being infected. The issue has since be resolved by the owners and management of Vanguard News.
The website of Vanguard newspapers, the number one Nigerian website, may harm your computer. This is according to alerts on Google search for results where pages on Vanguard website appears.
Over the past hour that I have been monitoring Google Search, I have noticed that all results containing Vanguard website includes the label This site may harm your computer. To simulate the event, just search for...
Internet Safety Tips for 2023
The internet is full of scams, fraud, and malicious software, ready to attack your electronic devices and computer. The bottom line is, you need to put proper safety measures in place to protect yourself from the increasing number of cybersecurity threats. Follow these basic internet safety tips in order to minimize chances of online attacks. You can also read our Internet Security tips for more ideas.
11 Top Internet Security Tips
1. Have a Good Password Policy
Take serious consideration in the passwords you use. Make sure to use good passwords for your email and other online accounts. Its also a good...
Internet Security Tips 2023 – Antivirus, Firewalls, Browsers
Whenever you access the internet, you are exposed to a number of security risks. Internet security is a burning topic today because of the increase in frequency of security breaches on the internet. We will share some good internet security tips to keep you safe online. The recent assault on companies and governments by organised hacking groups stealing valuable information of customers and clients has made internet security and even bigger issue.
Truth be told, most of us are defenseless against some of the internet security threats, especially against organised hacking groups. This is because these groups do not attack...
Yahoo Mail Boosts Security with HTTPS Encryption
Yahoo has now automatically rolled out HTTPS for its mail services meeting a January 8 deadline it had set for itself last year. If you visit your Yahoo mail on mobile or PC you will notice that it is now HTTPS. The new security upgrade is available as a default and will offer improved security to Yahoo mail users.
Yahoo mail's HTTPS uses stronger 2,048-bit encryption keys to secure certificates used to protect communications between the web server and your web browser. This will make it a lot harder to decipher intercepted emails.
According to Yahoo, this new security upgrade will...
How to Keep your Data Safe and Protected
When technology came in, nobody thought it would turn our lives upside down. At the beginning, it was all win-win situation as we were only focused on the convenience we were offered and neglected the negatives of it.
Data security has now become the biggest threat of this century. People have made millions just by stealing someone else’s data and using it for what not purposes.
Therefore, this obviously leads you to take some remedy steps before you face some unwanted consequences.
Lock your Computer:
Although the basic password locking option isn’t totally reliable, it still works as a barrier and prevents anyone...
3 Tips For Choosing The Best Wireless Router For Your Home...
Almost all of us now own a wireless Wi-Fi router and this is one of the most common devices that is used by everyone in the world yet we do not pay much heed on the quality and performance of the router we have.
Instead we all most of the times complain about how slow the internet is and how weak are the signals. Well, have you ever even for a second thought about your Wi-Fi router?
Maybe it’s high time that you should replace your old Wi-Fi router with a new one or maybe you should look into the major...
How to Stay Secure Online using a VPN
You may have come across several blogs highlighting how VPNs are a must these days. But they do not specify how VPNs can be used to actually stay safe and secure online.
It is no different than knowing how to drive in theory, but when it comes to practicality you have zero experience.
If you truly value your online security and anonymity, you must use a VPN without thinking twice. As for how it is to be used for security-related issues, here are a couple of use cases for your consideration.
Unlock the Internet
Similar to how you unlock new stuff in games...
How Can VoIP Enhance the Customer Experience? (Infographic)
No matter what line of business you’re in or how much of a budget you have, the satisfaction of your customers is crucial to the success of your company. With unprecedented levels of competition and instant avenues for the provision of unbiased feedback, it has never been more vital for businesses to keep their customer base happy, as a company’s reputation can make a huge difference in the retention, acquisition or losing of customers.
We came across an infographic from Paradyn which explains why VoIP phone systems enhance customer experience and make it far easier for them to receive a...
Best VPN for Apple TV in 2023, Compare Prices
What are the best VPN for Apple TV? Streaming media players like Apple TV allow people cast streaming on the TV from Mac devices. The experience with Apple TV, at first, may seem to be perfect; however, it can also be followed with different obstacles and limitations.
For instance, you may come across streaming that is geo-blocked in the country you are in, or you may become a target of cyber-attacks and the list of the risks can go on.
To avoid such problems, you can use VPN, which will smoothen your overall Apple TV experience and can open up many...
What You Should Know Before You Invest In VPN Services
The online space has become a breeding ground for thieves to fully manifest their wickedness. This has led to a deep need for online privacy by most internet users and has driven many to take up Virtual Private Network (VPN) services to protect their identity and their data.
You probably are interested in VPN services yourself. If that’s the case, here’s what you need to know before you invest in best VPN services:
1. The Technical Security Aspect
A VPN service that you should invest your money in should be packed with the best security features like split tunneling, Tor compatibility, kill...
Cyber Cafe Internet Security, Stay Safe Online
Security is a very important issue on the internet today. Browsing the internet often comes with security risks that some internet users are not even aware of. Your internet security risks increases tremendously if you browse using public PCs as found in cyber cafes.
A Cyber cafe (a.k.a Internet Cafe) is a place where internet applications are accessible to the public. Customers buy airtime in order to have access to the internet via PCs available in the internet cafe LAN network. The airtime contains a password for logging into the PC.
Customers can also come with a laptop and connect to...
Data Protection Should Be a Top Priority for Today’s Businesses. Here’s...
With cybercrimes reaching a new level of sophistication, data theft and ensuing criminal activities have rapidly escalated over the years. This has placed an increasing focus on data protection, and the responsibilities of businesses to safeguard data placed in their hands.
According to a report by Risk Based Security, 2019 saw a staggering 33% increase in data breaches. This doesn’t come as a surprise considering the number of high profile scandals that came into light during the year, from the Capital One data breach to compromised data of Facebook users.
What type of Business should Prioritize Data Protection?
Certain industries by nature...
Everything you Need to Know about VPNs
If you’re looking for a way to protect your online privacy and security, then a Virtual Private Network (VPN) may be just the solution you need.
A VPN is a powerful tool that can help you protect your data and identity from hackers, government surveillance and data collection companies. It also gives you access to geo-restricted content, allowing you to browse the web from any location.
In this article, you’ll find out everything you need to know about VPNs and how they work, including their benefits, drawbacks, and how to choose the right one for your needs. So, if you’re ready...
CyberGhost VPN: Stay Safe and Secure
The CyberGhost VPN for Windows is designed carefully and specifically to improve upon user interface, usability and keeping an eye on the accessibility features.
Therefore, the application has been reduced to the system tray interface, as with just a click on the icon, all six profiles are released so that the user selects the best option feature and quickly activates what he prefers.
You are also able to access pre configured profiles or connect directly to any country that CyberGhost has a server in. You always have full control over the additional profile properties, as each connection is built with the...
Getting Started with Access Control Policies
Each year, cyber-attacks and data hacks cost small and medium-sized businesses over $2 million a year. While most of these attacks are perpetrated by outside sources, there are instances when the employees a business employs will be responsible for a data breach. This is why monitoring and restricting the access your team has to certain sensitive information is important.
For most business owners, coming up with comprehensive access management policies is a bit overwhelming. It is hard to tell what information team members, vendors and third-parties will need to do their jobs.
If you are struggling with the development of...
8 Creative Ways to Improve Your Computer’s Security
Identity theft runs rampant in the U.S. and around the globe. Much of this theft happens via the use of computers. Tech makes life easier in many ways but also presents additional risks.
What can users do to reduce the risk of a security breach on their computer resulting in identity theft?
Taking the following precautions can significantly reduce the chances of falling victim of computer-based identity theft.
1. Set Up User Permissions
When purchasing a new computer, few people take the time to set account permissions. However, doing so can reduce the risk of unknowingly downloading and installing malware, especially when several...
How to Keep yourself Safe from Hackers and Cons Online? Here...
The internet has become more than just a virtual space where you can search for basic things by typing a few words into Google’s search bar. It’s a whole world now with social media profiles, shopping stores, businesses, and much more thriving.
This means that like the real world, there are burglars out online as well. These cybercriminals are always on the lookout for your personal and financial details.
Did you know that hacker attacks occur every 39 seconds in the United States? Not only are those who mean to invade your privacy but even marketers are constantly digging through your...
How to Find a Reliable Public Proxy
The proxy world is diverse and full of opportunities, provided you have the means of navigating it and finding the best services to meet your needs. A simple Google search will reveal a plethora of proxy providers, and if you wait a couple of hours and perform the same search with the same keywords, you are likely to come across more proxy options.
Therefore, it is critical to select a reliable proxy provider to meet all your expectations without compromising your personal data. When it comes to making a choice, most people will go for private proxies, not knowing that...
7 Types of Firewalls and Main Facts About Them
Security of network connection is one of the most important things to keep an eye on in the business. If your company’s equipment isn’t protected, it can be easily accessed from any computer in the world with just a few tools and a bit of knowledge. So, you need some kind of a guardian that will ensure that the connection is safe.
That’s why firewalls exist. They are devices or programs that block harmful network packages, thus not allowing them to get into the computer. However, while there are many types of firewalls of different forms and specifics, it’s important...
How SSN can be used for Identity Thefts?
The Social Security Number, commonly known as SSN, is a unique 9-digit number that is assigned to every citizen of the United States. The major purpose of this number is to track your identity, your income details, and your work experience.
How to Get Your SSN?
Getting your SSN i now so simple. You can either visit the official website portal or seek the help of an agency to get your Social Security Number. Seeking government filing assistance helps you get your SSN card easily.
Whenever you start your career, or you want to take advantage government benefits, you must submit your...
User Data Surveillance is Heading IOT Towards Disaster
It is time that we come out of our imaginary world and create a perfect one, where not even a single IOT device fails. IOT organizations are quite optimistic that their devices will touch the skies, and by 2020 there will be 20 billion devices globally. However, while all these optimistic approaches regarding IOT’s future do look promising, there is a lot of effort required in reality.
One thing is for sure though, the usage of IOT devices is increasing nowadays. This has allowed us to analyze the TRUE performance of such technologies, and the signs are not good at...
How to Secure Personal Information from Hackers
In recent years, Internet security protocols have been ramped up to counter rapidly evolving threats. Many users are connecting to the Internet using unsecured connections. Browser-equipped smartphones and tablet computers have made Wi-Fi hotspot usage increasingly popular.
As a result, hackers have more opportunities to intercept personal data. Identity theft has thus become extremely common.
There are ways, however, that users can protect themselves from hackers and people with malicious intent. Internet users should be aware of and utilize these safeguards.
Antivirus Software
Every computer device should have antivirus software installed. Spyware, malware and Trojan horse viruses can be used to gain access...
What Should CISOs Be Thinking About in 2022?
The past few years have shown us, based on enterprise network security statistics and also information from SMEs, that everything we thought we knew about cybersecurity and the threat landscape is either no longer relevant or is changing so quickly that it can feel impossible to keep up. This leaves CISOs with a lot on their plate in 2022.
However, at the same time, it can be exciting for CISOs to meet these challenges head-on and see that increasingly cybersecurity is something that’s an organizational and cultural goal as well as being a technical objective.
The following are some things CISOs...
Let’s Help you in Getting Certified for Cyber Security
CompTIA’s Security+ is a security certification which is well known and respected. An individual with this certification is known to have immense knowledge and expertise in security-related disciplines.
On the other hand, Security+ is an entry certification level examination where candidates having at least 2 years of experience in the network security field can obtain the Network+ certification.
Top IT leaders who obtain this certification have expertise in areas such as threat management, identity management, security risk, network access control, identification and mitigation, cryptography, security systems, and security infrastructure.
This credential certification (CompTIA Security+) follows the standard for ISO 17024 and is...
How Kids Can Make the Right Use of Tech and not...
Kids start using the internet and digital devices like smartphones and tablets at a much earlier stage in their life. This could expose them to apps that are addictive and result in lack of concentration and focus. However, are there ways kids can make the right use of these powerful technologies without getting addicted. We look at this in this article.
Of course, if kids are to use their devices and the immense power that the internet and modern technology right they will surely need the help of their parents. One crucial step for the parents is to use parental...
Hacking an Android Phone By Sending A Link
It is needless to say that smartphones have become an essential part of our lives. From communication to entertainment to shopping, we need our smartphones for every little thing we do.
We also use our smartphones to store sensitive and private data like card details, passwords, etc. This makes smartphones the prime targets of hackers.
A hacker can use different ways to get to your phone. One of the ways is by sending a link. If you are an Android user, you should be careful of what links you receive on your phone. That’s because this method is more commonly used...
Protect Your Digital Self in a Few Minutes a Day
You’ve probably grown up hearing the expression, “an ounce of prevention is worth a pound of cure.” It’s as old as the ages, but it still applies today. And never has an ounce of prevention been as important as it is when it applies to protecting digital self on the Internet.
There are hackers, scammers, catfishers and others lurking on the net just waiting for you to make a simple mistake, and they’re taking your identity, your financial information and ultimately your money.
Here’s the good news – there are some things you can do to protect your digital self in...
Why Your Company Needs Ransomware Attack Software Solution
Malware or ransomware attacks are implemented through viruses inside companies' systems and networks to get a hold of their data. These software corrupt systems to hold the data hostage in them until a sum is paid to the hackers.
The ransomware technique for getting money from big or small firms alike is on the rise these days, and the craft is engulfing several companies under its threatening umbrella.
The after-effects of such a crime aren't pleasant either; hence a company should always be prepared for such an attack. Below are some other important reasons why your company needs to be ready...
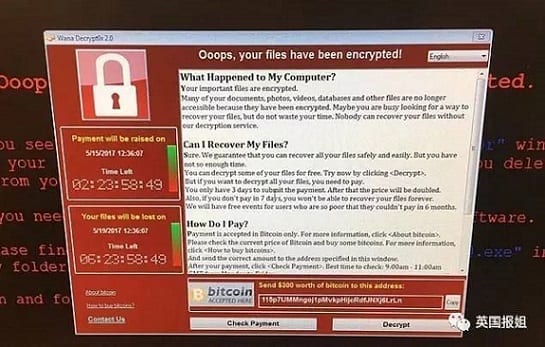
Ransomware: What you should know about them
The WannaCry cyber attack that targeted Microsoft Windows operating system in 2017 infecting over 200,000 computers in over 150 countries, drew greater attention to ransomware and software security in general. So what is ransomware and what should you know about it? Read on!
About Ransomware
Ransomware is a type of malware that denies a victim access to data on their device until a ransom is paid. This malicious software could also issue a threat, such as to delete or destroy the data, in the event of the victim failing to make necessary payment.
You could simply think of a ransomware attack as...
More Cryptojackers on the Horizon
While you click on yet another article about the threats of ransomware, a new, more insidious form of malware has taken over the web. Cryptojackers might sound like ransomware, but they operate in nearly the exact opposite way: Instead of making their presence known fast, cryptojackers try to hide themselves deep in your processor.
And, instead of demanding cash for your data, they couldn’t care less about what salacious pictures are stored on your device; they are draining your bank account indirectly.
If this is the first time you’re hearing about cryptojackers, that’s bad news - you probably already have one...